Our secured services are the best in the industry and comply with all the regulatory standards to ensure safe and secure business.
NeuralSEC Assessments
NeuralSEC Assessments
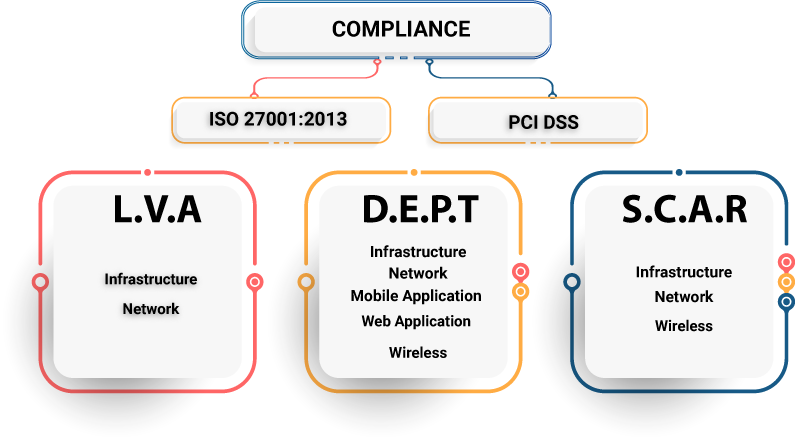
Holistic View Of Our Security Services
ISO 27001:2022 (ISO 27001)
Certification Audit & Implementation
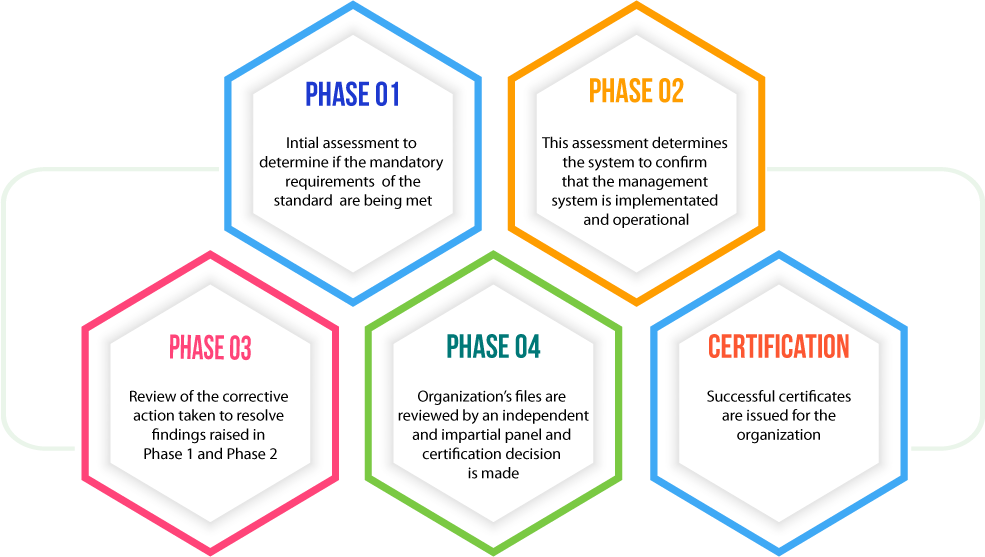
SO 27001 is the international standard that is recognized globally for managing risks to the security of information you hold. ISO 27001 certification allows the organization to provide proper proof that all the information is being securely managed by their clients and other stakeholders. ISO 27001:2022 (ISO 27001) (the current version of ISO 27001) provides a set of standardized requirements for an Information Security Management System (ISMS), which is to be followed by the organization.
The ISO ISO 27001:2022 (ISO 27001) standard adopts a process-based approach for establishing, implementing, operating, monitoring, maintaining, and improving the organization’s Information Security Management System (ISMS).
The ISO 27001:2022 (ISO 27001) standard and ISMS provide a framework for information security management best practices that helps organizations in:
- Protecting client and employee information
- Managing risks to information security effectively
- Achieving compliance with regulations such as the European Union General Data Protection Regulation (EU GDPR)
- Protecting the organization’s brand image
Benefits
- Secure Confidential Information
- Secure Exchange of Information
- Compliance with Regulations
- Competitive Advantage
- Enhanced Customer Satisfaction
- Protects the Organization
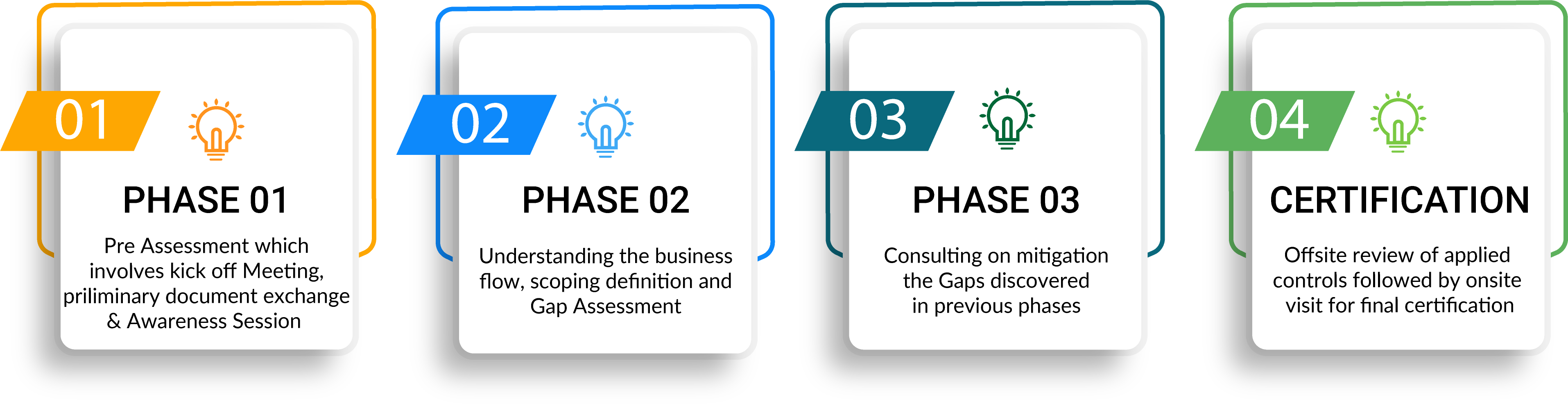
ISO 27001 Certification Process
Deliverables
- Documentation Review of organization’s policies, procedures, standards, and guidance documentation
- Evidential Audit that verifies the policies are being complied with, that procedures and standards are being followed, and that guidance is being considered
- Management Review to ensure that corrective actions and improvements are implemented as necessary
PCI DSS
Audit & Implementation
Payment Card Industry Data Security Standard (PCI DSS) is an information security standard for organizations that handle monitory transactions via credit or debit cards. This standard maintains a very strict set of requirements that are intended to ensure that all organizations store, transmit or process credit and debit card information maintain a secure environment.
PCI DSS certification is also considered the best way to safeguard sensitive financial data and information, thereby helping businesses run securely and smoothly. This helps in building a long lasting and trusting relationships with their customers.
Benefits
PCI DSS Compliance Level
- Reduces risk of data breaches
- Protects Customers
- Secure Exchange of Information
- Imparts a Mindset of Security
- Competitive Advantage
- Imparts a Mindset of Security
- Improves Brand Reputation
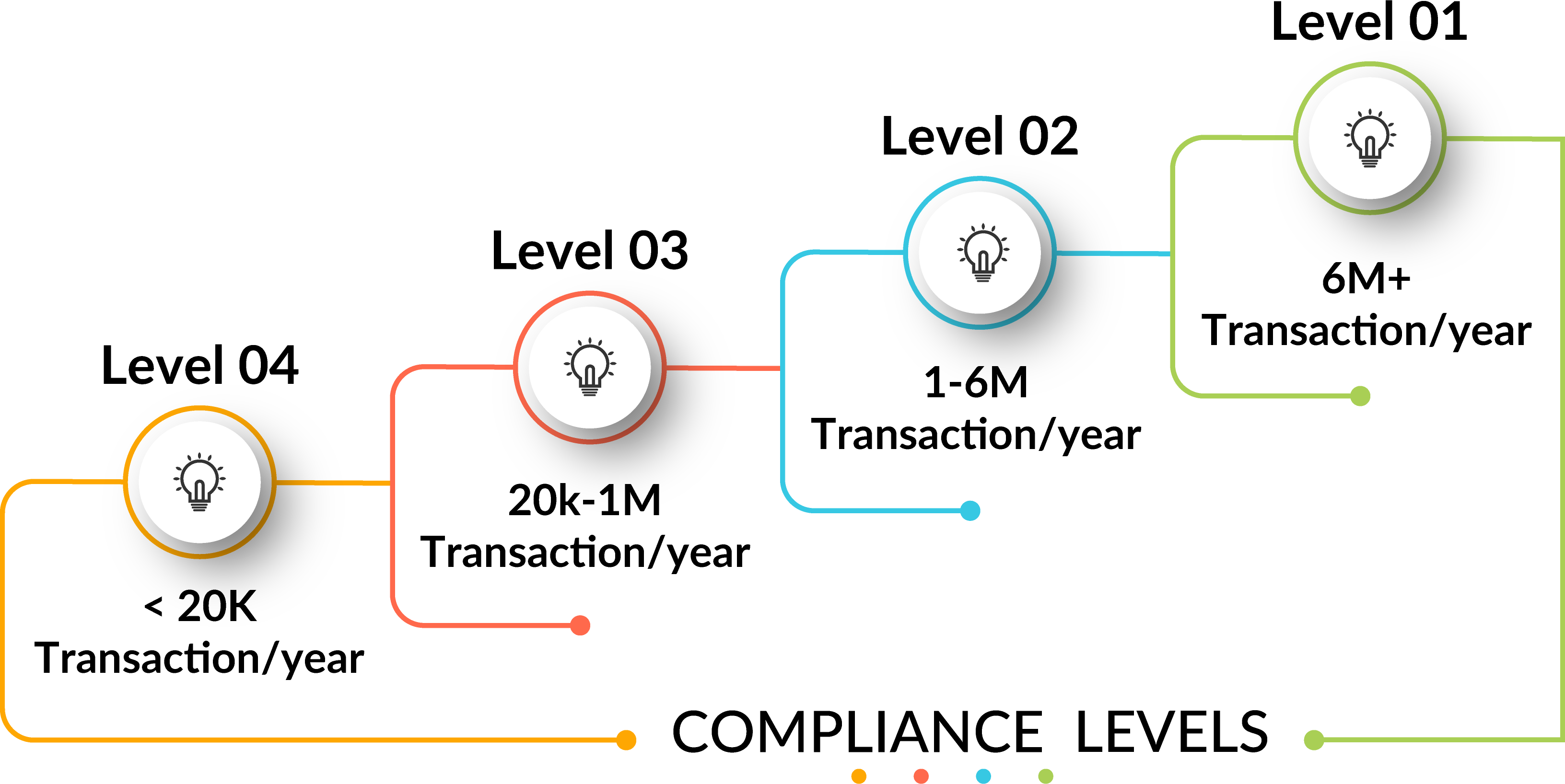
PCI DSS Compliance Process
Deliverables
- A detailed Analysis Report containing:
- Gap assessment of the 12 security controls of the PCI DSS standard
- Review of all policy and procedures to determine proper PCI coverage
- Review of Gaps discovered and tailored remediations of all Gaps for faster resolution
L.V.A
Litmus Vulnerability Assessment
Litmus Vulnerability Assessment (L.V.A) serves as a benchmark to evaluate the organization’s IT infrastructure for known vulnerabilities, in order to bring forth the current security posture of the organization’s IT assets. This process involves a combination of automated and manual techniques with varying degrees of rigor with an emphasis on providing comprehensive coverage of the security state.
Litmus Vulnerability Assessment (L.V.A) targets different layers of technology such as network-layer, host-layer and service-layer. The exercise, upon its completion, provides prioritized risk-based step-by-step actions to fix the vulnerabilities identified within the IT systems.
Benefits
- Detect security weaknesses before attackers do.
- A listing of vulnerabilities for each device and application.
- Preparation for future upgrades.
- Established security baseline for later assessments.
- Evaluation of technical risk for your Infrastructure and application.
- Early identification saves the future cost of recovery and time.
- Misconfiguration identification.
Litmus Vulnerability Assessment Types
Authenticated L.V.A
Authenticate Litmus Vulnerability Assessment (L.V.A) determines how secure the asset in scope is from an inside vintage point. This method is used to identify what needs to be done to reduce the risk after an attacker gains access to the network or a user account. Insider threats are also identified during this testing.
Unauthenticated L.V.A
Unauthenticated Litmus Vulnerability Assessment (L.V.A) assesses the security of an asset from an outside perspective. This analysis identifies what a malicious attacker could access without acquiring inside access to the asset.
Litmus Vulnerability Assessment Process
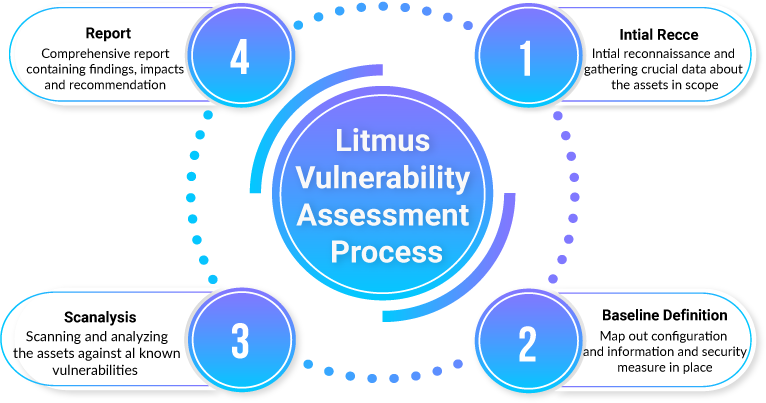
Initial Recce
In this phase, the target is identified, with various scanning techniques and running services are discovered and tested for their version and type.
Baseline Definition
Once relevant information is gathered, the next step is to identify the end points along with their business impact after compromise. This helps in developing a plan of action where we rank the end points in the order of perceived value.
Scanalysis
Each endpoint will be tested for known vulnerabilities via automated tools and later verified by manual analysis. The extent of vulnerability is then assessed, including the level of weakness and the sensitivity of the information it might expose.
Report
Once the testing is complete, Neural IT delivers a detailed analysis and threat report, including executive summary, identified vulnerabilities and risk rating, along with detailed remediation steps.
L.V.A Deliverables
A Detailed Vulnerability Assessment Report With:
- Assessment of the security measures currently in place compared with industry practices
- Identification of vulnerabilities on the systems and processes that pose a security risk before attackers identify them.
- Defined level of risk that exists on the network/application.
- All the vulnerabilities identified will be rated from low to critical on the basis of their likelihood and their impacts.

Our USP
A Detailed Vulnerability Assessment Report With:
- Assessment of the security measures currently in place compared with industry practices
- Identification of vulnerabilities on the systems and processes that pose a security risk before attackers identify them.
- Defined level of risk that exists on the network/application.
- All the vulnerabilities identified will be rated from low to critical on the basis of their likelihood and their impacts.

D.E.P.T
Deep Elemental Penetration Testing
Deep Elemental Penetration Testing (D.E.P.T) is a type of security testing where the digital assets of the organization are exploited to understand the impact of the vulnerabilities found on them which the attackers can take advantage of. A penetration test takes the perspective of an outside intruder or an internal individual with malicious intent, this way the organization can better understand the risk to their IT environment.
The methodology for penetration testing utilizes vulnerability Assessments as well and with few extra steps which involve exploiting the target, to prevent your organization from possible breaches and reinforce existing security controls against a skilled attacker, we offer penetration testing services based on a custom plan of a multistep attack that targets custom network infrastructure and applications.
Deliverables
A Detailed Penetration Testing Report Including:
- Exploitation of vulnerable services, applications and devices which pose a threat to the IT environment of the organization Strategic, practical and easy-to-understand remediation to patch the vulnerable services
- A comprehensive report including Executive Summary, for understanding the business impact of the vulnerabilities and Technical Summary of findings with tailored steps for remediation
- Strategic recommendations to ensure that the IT infrastructure is secure against attacks based on your unique business requirements and industry best practice
Benefits Of Deep Elemental Penetration Testing
- The ability to prevent incidents that could adversely affect the company's image and customer safety
- Reducing the risks of information leakage and unauthorized access
- Detection of all critical threats to digital assets of the organization
Deep Elemental Penetration Testing Types
Black Box Testing
This is done to test as a third part attacker. Black box testing doesn’t require any knowledge of the internal path, working or structure of the asset being tested.
Grey Box Testing
In this type of testing limited knowledge of the internal working of the system is provided to test as a user with access to the internals
White Box Testing
White Box testing provides a comprehensive of both internal and external vulnerabilities and focuses more on the process of the application.
Deep Elemental Penetration Testing Process
The penetration testing process picks up from where Litmus Vulnerability Assessments left off. Thus, the first three phases remain the same and the next phases exploit the vulnerability.
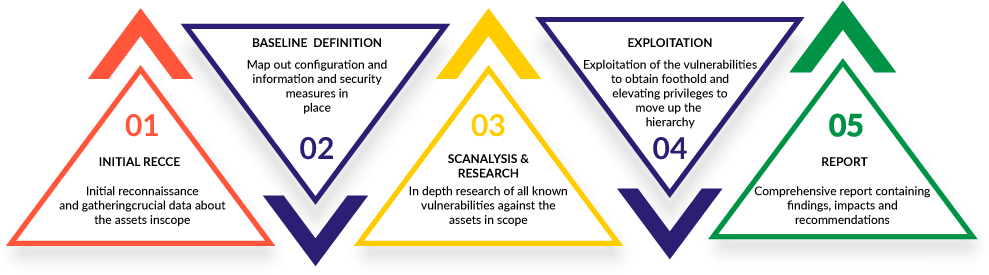
Initial Recce
In this phase the target is identified with various scanning techniques and running services are discovered and tested for their version and type.
Baseline Definition
Once relevant information is gathered, the next step is to identify the end points along with their business impact after compromise. This helps in developing a plan of action where we rank the end points in the order of perceived value.
Scanalysis & Reseaech
Each endpoint will be tested for known vulnerabilities via automated tools and later verified by manual analysis. The extent of vulnerability is then assessed, including the level of weakness and the sensitivity of the information it might expose.
Exploitation
After the vulnerabilities are identified the only thing left is to attack them. The vulnerabilities now will be exploited just as in a real-world attack. After successful exploitation, based on the type of access provided and the type of information disclosed the risk will be re-evaluated.
Report
Once the testing is complete, Neural IT delivers a detailed analysis and threat report, including executive summary, identified vulnerabilities and risk rating along with detailed remediation steps.
Wireless Deep Elemental Penetration Testing Process
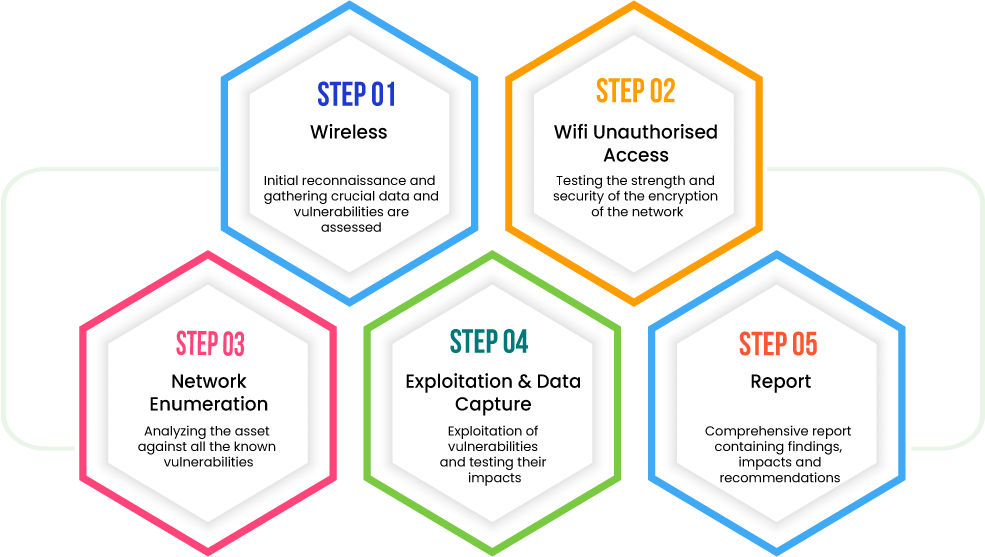
Wireless Recon
This is the very first phase in the entire Wireless Penetration Testing Process where Information about the target wireless network is gathered like BSSIDs, SSIDs, Encryption security is analyzed. Based on the information gathered vulnerabilities are assessed.
Wi-Fi Unauthorized Access
In this phase, the Wi-Fi security will be tested for unauthorized access, the strength of the security encryption used on the network will also be tested.
Network Enumeration
Once the attacker gains unauthorized access to the network, he will gather more information about the network, its topology, and how the machines interact with each other.
Exploitation & Data Capture
In this phase the network will be tested for man-in-the-middle attacks and the data flowing in the network will be captured to test if sensitive data is flowing without any protection and what the attacker can do with it.
Reporting
After the testing, a detailed report will be generated which will comprise all the vulnerabilities found during the testing with their remediation.
S.C.A.R
Secure Configuration Architecture Review
The network infrastructure of the organization develops over many years. While this development is a direct response to the changing needs of the business, security has improved in many respects, our Secure Configuration Architecture Review (SCAR) is conducted by systematic examination of all layers of an organization's network. We will examine the existing network topology and deployment of security controls within the organization such as firewalls, IDS/IPS, network partitions,
and make recommendations to increase the effectiveness of security controls.
Our systematic approach is to the evaluation of the current security structure which ensures a detailed review of the current architecture, technology, and security policy of the organization, management practices, and planned changes. We identify network and design weaknesses in security, performance, scalability. After the review suggestions to improve the security architecture will be submitted along with business objectives, your organization's security policy, and industry best practices.
Benefits Of Secure Configuration Architecture Review (S.C.A.R)
- Provides a detailed analysis of currently deployed application, system and the entire IT infrastructure
- Helps in identifying weaknesses and provides recommendations to reduce the attack surface
- Enables the organization to scale with a strong secure IT infrastructure
Secure Configuration Architecture Review (S.C.A.R) Deliverables
- Review the latest threat risk analysis report.
- Analysis of current IT networks, information flow according to business needs and points of access to information.
- Analysis of current security controls and procedures for various security management areas.
- Analyze existing network security architecture including topology & configuration, and security components.
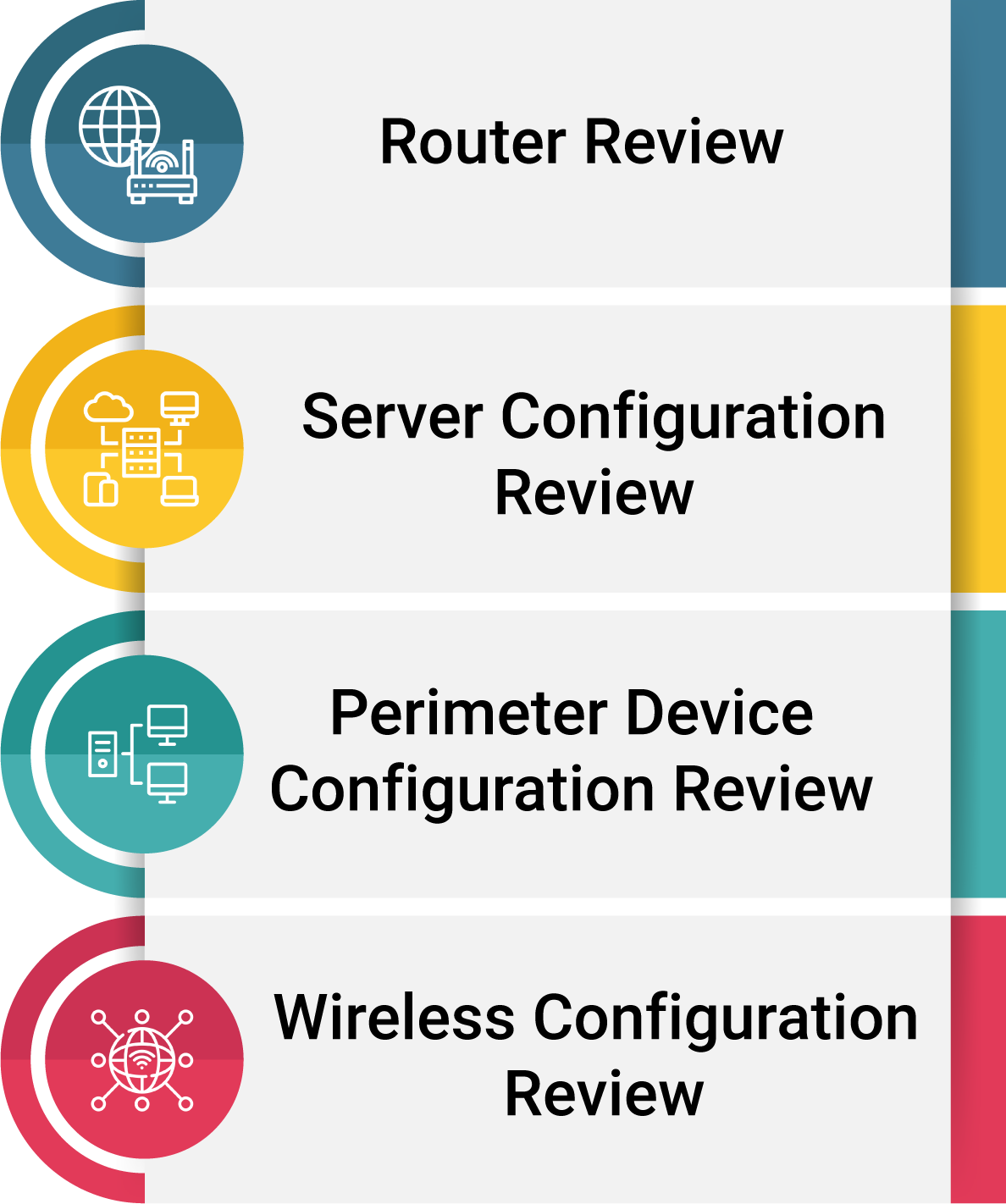
Secure Configuration Architecture Review Includes
Vulnerability Risk Definition And Criteria
The risk ratings assigned to each vulnerability are determined by averaging several aspects of the exploit and the targeted asset, including the difficulty, and criticality of the vulnerability.
Critical
Critical risk vulnerabilities will have a crippling effect. Vulnerabilities of this level usually result in complete compromise of the affected host along with the possible environment it resides on. In most instances, the exploit is already available publicly and requires little to no tweaking while exploiting.
High
High risk vulnerabilities will be able to access potential sensitive information or bypass restrictions to gain unauthorized access. The severity is reduced based on the type of information leaked or the type of access gained.
Medium
Medium risk vulnerabilities will most often require further determination and technical ability to create a noticeable effect on an organization’s business. This includes Denial of Service attacks which can be difficult to set up, or vulnerabilities that need further chaining to social engineering or access to backend infrastructure to have a bigger impact.
Low
Low risk vulnerabilities have very little impact on an organization’s business. Exploitation of such vulnerabilities would either require local privileged access or to be used in combination to other findings.
Informational
Informational vulnerabilities don't really pose a huge threat to the assets in scope. They are included however, as they can be used to chain with other vulnerabilities to further exploit the targeted asset.

